Getting Started with BeyondTrust Privileged Access Management (PAM)
In today's complex digital landscape, securing critical assets and data is paramount for every organization. As cyber threats become more sophisticated, traditional security measures often fall short, leaving vulnerabilities that attackers can exploit. This is where Privileged Access Management (PAM) steps in, and among the leading solutions, BeyondTrust stands out. If you're looking to fortify your organization's defenses and streamline privileged access, understanding BeyondTrust PAM is your crucial first step.
What is BeyondTrust Privileged Access Management?
BeyondTrust Privileged Access Management (PAM) is a comprehensive suite of security solutions designed to protect, manage, and audit privileged accounts and sessions. Privileged accounts, such as administrator, root, or service accounts, possess elevated permissions that allow them to make significant changes to systems and access sensitive information. If compromised, these accounts can provide attackers with the keys to your entire digital kingdom.
BeyondTrust PAM addresses this critical risk by providing:
- Privileged Password Management: Securely stores, manages, and rotates privileged credentials, eliminating hardcoded passwords and reducing the risk of theft.
- Endpoint Privilege Management: Removes local administrator rights from end-users while still allowing them to perform necessary tasks, effectively reducing the attack surface on workstations and servers.
- Secure Remote Access: Provides controlled and audited remote access for vendors and internal users, ensuring that all remote sessions are secure and monitored.
- Session Management and Monitoring: Records and monitors all privileged sessions in real-time, offering forensic capabilities and immediate alerts on suspicious activity.
- Vulnerability Management: Identifies and remediates vulnerabilities across your IT environment, integrating with PAM to prioritize and secure at-risk assets.
By centralizing control over privileged access, BeyondTrust PAM helps organizations achieve compliance, reduce their attack surface, and enhance their overall security posture.
Market Share of BeyondTrust Privileged Access Management
PAM is a fast-growing segment in cybersecurity. According to recent industry analysis:
-
BeyondTrust, IBM, and CyberArk collectively hold ~24% of the PAM market (2024) — showcasing strong positions among competitors.
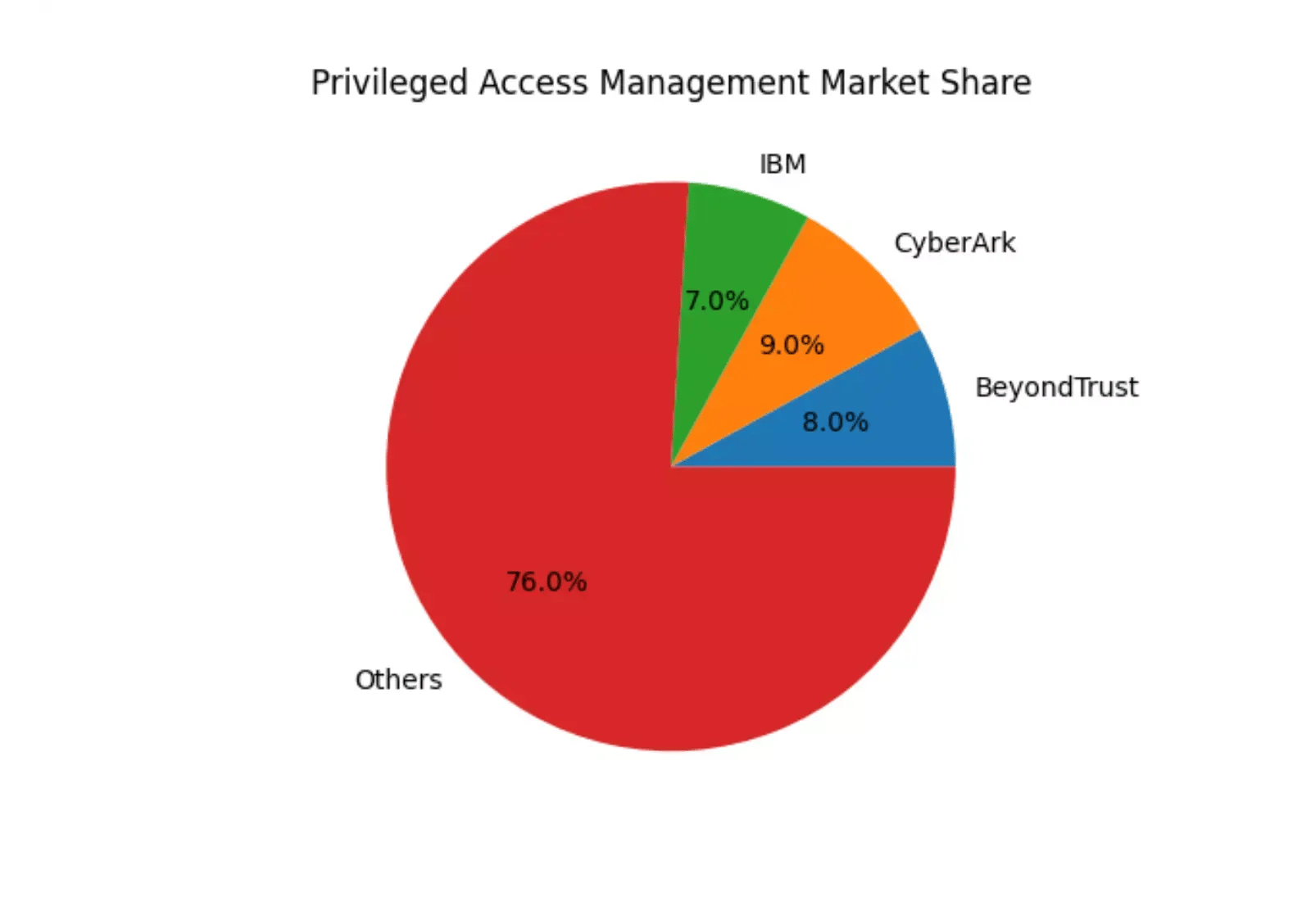
BeyondTrust’s share is part of the leading 24% cluster among top vendors.
Note: Actual market percentages may vary across surveys.
Why Take BeyondTrust Privileged Access Management Training?
Investing in BeyondTrust PAM is only half the battle; effectively implementing and managing it requires specialized knowledge. BeyondTrust PAM training offers numerous benefits:
- Maximize Your Investment: Proper training ensures your team can leverage the full capabilities of the BeyondTrust suite, maximizing your organization's return on investment in the technology.
- Enhance Security Posture: A well-trained team can configure and maintain the system to its optimal security settings, effectively mitigating risks from privileged account misuse.
- Ensure Compliance: Many regulatory frameworks (e.g., GDPR, HIPAA, PCI DSS) mandate strict control over privileged access. Training helps your team implement and manage BeyondTrust PAM in a compliant manner.
- Boost Operational Efficiency: Understanding the system inside out allows for smoother operations, faster troubleshooting, and efficient management of privileged accounts and sessions.
- Career Advancement: For individuals, BeyondTrust PAM skills are highly sought after in the cybersecurity industry, opening doors to advanced career opportunities.
Who Can Do BeyondTrust Privileged Access Management Training?
BeyondTrust PAM training is beneficial for a wide range of IT and security professionals, including:
- Security Engineers and Architects: Those responsible for designing, implementing, and maintaining an organization's security infrastructure.
- System Administrators: Professionals who manage servers, networks, and applications, and deal with privileged accounts daily.
- IT Auditors: Individuals who need to understand how privileged access is controlled and audited for compliance purposes.
- Compliance Officers: Professionals ensuring the organization adheres to relevant industry regulations and standards.
- DevOps Engineers: Those working in environments where automation and secure access to development and production systems are critical.
- Cybersecurity Analysts: Professionals who monitor and respond to security incidents, needing to understand privileged access logs.
- Anyone interested in a career in cybersecurity or identity and access management.
Course Outcome
Upon completing BeyondTrust PAM training, participants typically gain the ability to:
- Understand PAM Fundamentals: Grasp the core concepts of Privileged Access Management and its importance.
- Navigate the BeyondTrust Platform: Become proficient in using the various components of the BeyondTrust solution (e.g., Password Safe, Endpoint Privilege Management, Secure Remote Access).
- Configure and Deploy: Effectively install, configure, and integrate BeyondTrust PAM solutions within an existing IT environment.
- Manage Privileged Accounts: Implement policies for password rotation, session recording, and access control.
- Monitor and Report: Utilize the platform's reporting and auditing features to ensure compliance and identify potential security threats.
- Troubleshoot Issues: Diagnose and resolve common issues related to BeyondTrust PAM deployments.
- Implement Best Practices: Apply industry best practices for privileged access security using BeyondTrust tools.
Career Opportunities in BeyondTrust Privileged Access Management
The demand for cybersecurity professionals with specialized PAM skills is soaring. Expertise in BeyondTrust PAM can lead to exciting and rewarding career paths, including:
- PAM Engineer/Administrator: Responsible for the day-to-day management and maintenance of the BeyondTrust PAM solution.
- Security Consultant (PAM Specialist): Advising clients on PAM strategies, implementing solutions, and providing expert guidance.
- Cybersecurity Architect: Designing enterprise-wide security solutions, often incorporating PAM as a foundational component.
- Identity and Access Management (IAM) Specialist: Focusing on the broader IAM landscape, with PAM being a critical subset.
- Security Operations Center (SOC) Analyst: Utilizing PAM logs and alerts for incident detection and response.
- Technical Trainer (BeyondTrust Products): Educating others on the effective use of BeyondTrust solutions.
Salary Package
Salaries for professionals with BeyondTrust PAM skills are highly competitive, reflecting the critical nature of the role. Experience plays a significant factor, with senior roles commanding substantial packages.
Here's an illustrative graph showing a typical salary progression based on years of experience in the BeyondTrust PAM domain.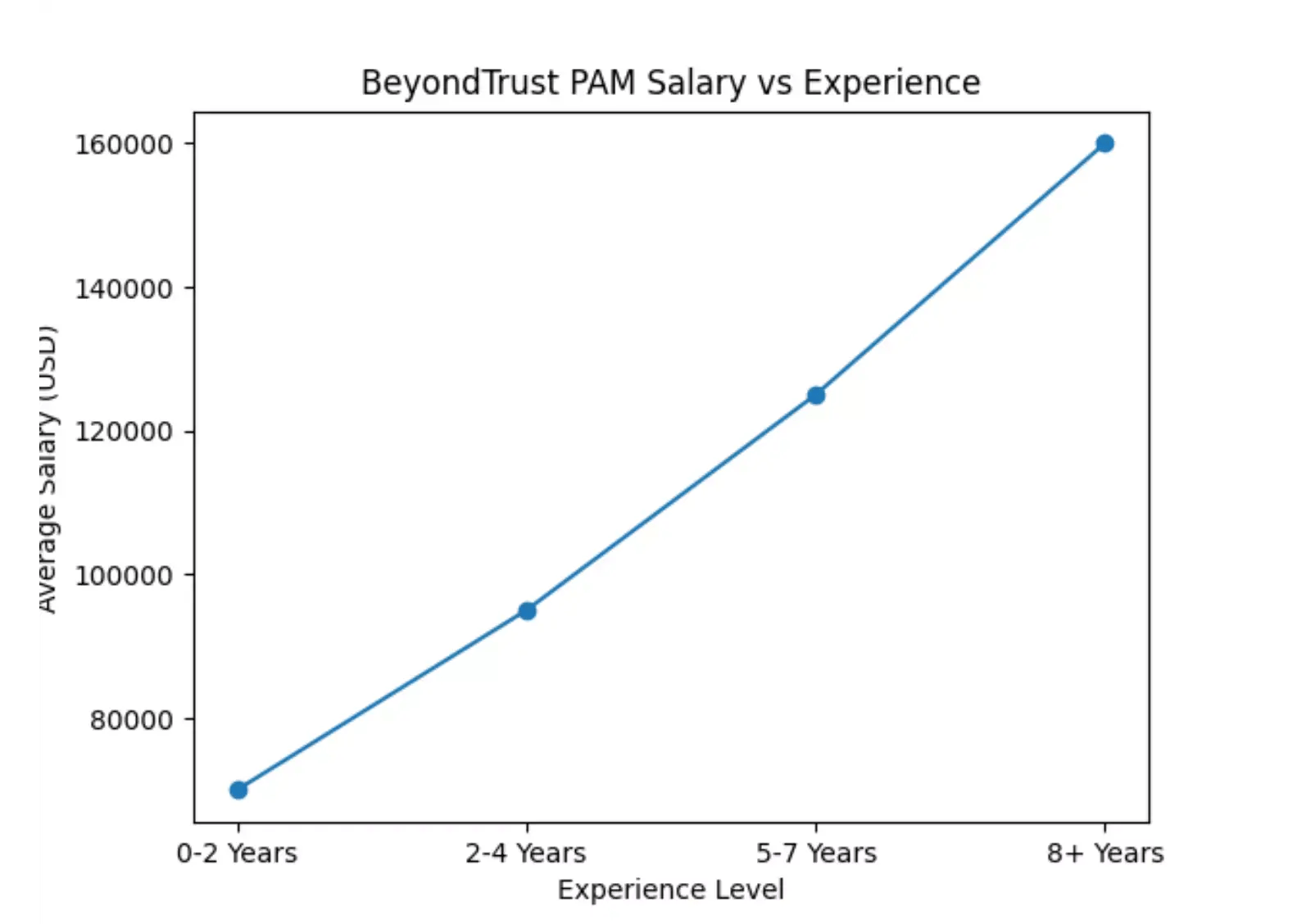
Note: Actual salaries can vary significantly due to factors such as geographic location, company size, specific responsibilities, certifications, and economic conditions.
Companies Hiring BeyondTrust Privileged Access Management Professionals
Given the widespread adoption of BeyondTrust PAM across various industries, a diverse range of organizations actively seek professionals with this expertise. These include:
- Large Enterprises: Financial institutions, healthcare providers, telecommunications companies, and retail giants all rely on robust PAM solutions.
- Government Agencies: Public sector organizations often have strict security requirements for privileged access.
- Managed Security Service Providers (MSSPs): Companies that offer cybersecurity services to other businesses frequently manage BeyondTrust for their clients.
- Consulting Firms: Cybersecurity consulting firms need specialists to help their clients implement and optimize PAM solutions.
- Technology Companies: Software development companies, cloud service providers, and IT integrators.
- Any organization with a significant IT footprint and a commitment to cybersecurity.
Many industries are actively hiring PAM talent, including:
🏢 United Airlines — Sr Analyst PAM role Glassdoor
🏢 Bank of America — PAM Analyst Glassdoor
🏢 UCLA & Marriott — Security engineers Glassdoor
🏢 Citigroup (Citi) — PAM Infrastructure roles Citi Careers
🏢 HPE — Senior PAM Manager HPE
... and many more worldwide.
Roles and Responsibilities
While specific duties can vary, a BeyondTrust PAM professional typically undertakes responsibilities such as:
- Implementation & Deployment: Installing, configuring, and integrating BeyondTrust components (e.g., Password Safe, Endpoint Privilege Management) into existing IT infrastructure.
- Policy Management: Defining and enforcing granular access policies for privileged accounts and users.
- Account Onboarding: Discovering and onboarding privileged accounts into the BeyondTrust system.
- Session Monitoring & Auditing: Monitoring privileged sessions in real-time, reviewing audit trails, and generating compliance reports.
- Troubleshooting & Support: Resolving technical issues related to the BeyondTrust platform.
- System Upgrades & Maintenance: Performing regular maintenance, patches, and upgrades to the BeyondTrust environment.
- Documentation: Creating and maintaining detailed documentation of configurations, policies, and procedures.
- Security Best Practices: Ensuring the BeyondTrust deployment adheres to security best practices and compliance requirements.
- User Training: Providing training and support to end-users and administrators on BeyondTrust PAM functionalities.
Steps to Prepare for BeyondTrust Privileged Access Management
To effectively prepare for a career in BeyondTrust PAM or to implement the solution within your organization, consider these steps:
- Foundation in Cybersecurity: Start with a strong understanding of fundamental cybersecurity concepts, including networking, operating systems (Windows, Linux), active directory, and common attack vectors.
- Learn IAM Basics: Familiarize yourself with Identity and Access Management (IAM) principles, including authentication, authorization, single sign-on, and multi-factor authentication.
- Explore BeyondTrust Resources: BeyondTrust offers extensive documentation, whitepapers, webinars, and free trials on their official website. Leverage these resources to get acquainted with their product suite.
- Hands-on Experience: Whenever possible, seek opportunities for hands-on experience. This could involve setting up a lab environment, participating in proof-of-concept deployments, or utilizing virtual training labs.
- Formal Training: Enroll in official BeyondTrust training courses or reputable third-party training providers that specialize in BeyondTrust PAM.
- Network with Professionals: Join cybersecurity communities, forums, and LinkedIn groups to connect with other PAM professionals and learn from their experiences.
- Stay Updated: The cybersecurity landscape evolves rapidly. Continuously read industry news, blogs, and security reports to stay informed about new threats and PAM advancements.
Certification
BeyondTrust offers certifications that validate a professional's expertise in their product suite. While the specific certification names and tracks may evolve, they typically cover areas such as:
- BeyondTrust Certified Professional (BTCP): Often an entry-level certification demonstrating foundational knowledge and operational skills across BeyondTrust products.
- BeyondTrust Certified Administrator (BTCA): For professionals responsible for the deployment, configuration, and day-to-day management of BeyondTrust solutions.
- BeyondTrust Certified Engineer (BTCE): Aimed at more experienced professionals who design, implement complex integrations, and troubleshoot advanced scenarios.
Obtaining these certifications demonstrates your proficiency to employers and can significantly boost your career prospects. Always check the official BeyondTrust website for the most current certification programs and requirements.
Conclusion
BeyondTrust Privileged Access Management is an indispensable tool in the modern cybersecurity arsenal, offering robust protection against one of the most critical attack vectors: compromised privileged accounts. For organizations, it's a strategic investment in security and compliance. For individuals, mastering BeyondTrust PAM opens doors to a dynamic and high-demand career path in cybersecurity. By understanding its capabilities, investing in proper training, and pursuing relevant certifications, you can position yourself or your organization for success in an increasingly threat-laden digital world.
You May Also Like
These Related Stories

Mastering SAP PM Unlocking the Potential of Plant Maintenance Training

How to Get Certified in Adobe Experience Platform
.png)

No Comments Yet
Let us know what you think